- SlotConfig[TargetKey].Bit13 must be set or
DeriveKeywill return an error. DeriveKeyalways returns an error if KeyConfig indicates that the slot contains an ECC private key, if the Configuration zone has not been locked, or if the TargetKey slot is individually locked using SlotLocked.- SlotConfig[TargetKey].Bit 12
- 0: The source key that will be combined with TempKey is the target key as specified in the command line (Roll Key operation)
- 1: The source key is the parent key of the target key, which is found in SlotConfig[TargetKey].WriteKey (Create Key operation).
- If SlotConfig[TargetKey].Bit15 is set, an input MAC must be present and have been
computed as follows:
-
SHA-256(ParentKey, Opcode, Param1, Param2, SN[8], SN[0:1])
where the ParentKey ID is always SlotConfig[TargetKey].WriteKey.
-
- If performing a Roll Key operation and KeyConfig[TargetKey].ReqAuth is one, then the
appropriate authorization must have been performed using KeyConfig[TargetKey].AuthKey
prior to the execution of
DeriveKey. If performing a Create Key operation and KeyConfig[ParentKey].ReqAuth is one, then the appropriate authorization must have been performed using KeyConfig[ParentKey].AuthKey prior to the execution ofDeriveKey.
Prior to execution of this command, the Nonce command
must have been run to create a valid nonce in TempKey. If KeyConfig.ReqRandom is one for
the source key, this nonce must have been created with the internal RNG or an error will be
returned. In all cases, Mode[2] must match the state of TempKey.SourceFlag or the command
will return an error.
If performing a Roll Key operation and KeyConfig[TargetKey].ReqAuth is
one, then the appropriate authorization must have been performed using
KeyConfig[TargetKey].AuthKey prior to the execution of DeriveKey. If
performing a Create Key operation and KeyConfig[ParentKey].ReqAuth is one, then the
appropriate authorization must have been performed using KeyConfig[ParentKey].AuthKey prior
to the execution of DeriveKey.
If an input MAC is required and KeyConfig[ParentKey].ReqAuth is one, then
the appropriate authorization must have been performed using KeyConfig[ParentKey].AuthKey
prior to the execution of DeriveKey.
If a parent key is involved in the operation (either
SlotConfig[TargetKey].Bit12 or SlotConfig[TargetKey].Bit15 are set) and
SlotConfig[ParentKey].LimitedUse is also set, DeriveKey returns an error if Counter[0] has
reached its limit. DeriveKey always ignores LimitedUse for the target
key.
For the
ATECC608A-TNGLoRaWAN, the DeriveKey command
can be run on Slot 0. Slot 13 is the parent key used for the
key derivation and an authorizing MAC is always
required.
|
Opcode |
Mode |
TargetKey |
Data |
Description |
|---|---|---|---|---|
| 0x1C | 0x00 | 0x00 0[Slot] | Optional MAC data | Use if TempKey Source was Random |
| 0x04 | 0x00 0[Slot] | Optional MAC data | Use if TempKey Source was fixed |
| Name | Size | Notes |
|---|---|---|
| Response | 1 Byte |
|
The key written to the target slot is the result of SHA-256 of the following message:
| # of Bytes | SlotConfig[12]=0 | SlotConfig[12]=1 |
|---|---|---|
| 32 | TargetKey | ParentKey |
| 1 | OpCode = 0x1C |
OpCode = 0x1C |
| 1 | Mode | Mode |
| 2 | TargetKey | TargetKey |
| 1 | SN[8] = Varies by vendor | SN[8] = Varies by vendor |
| 2 | SN[0:1] = 0x01 0x23 | SN[0:1] = 0x01 0x23 |
| 25 | Zeros | Zeros |
| 32 | TempKey.Value | TempKey.Value |
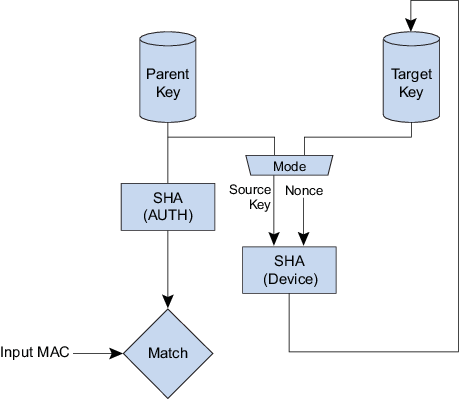
The data flow for this command is illustrated in Figure 1.
DeriveKey Command