3.1.3 ICM Peripheral Library Configurations
The ICM peripheral library can be configured through MCC. Following is the MCC configuration window and a brief description.
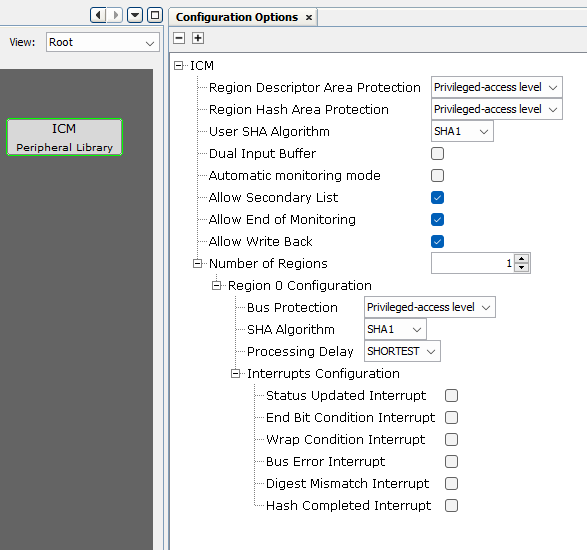
- Region Descriptor Area
Protection:
- Indicates the value of the protection attribute propagated on the system bus when the ICM accesses the Descriptor Area. Possible values are user-access level and privileged-access level.
- Region Hash Area
Protection:
- Indicates the value of the protection attribute propagated on the system bus when the ICM accesses the Hash Area. Possible values are user-access level and privileged-access level.
- User SHA Algorithm:
- This is used when the initial hash value is required. Supported SHA algorithms are SHA1, SHA256 and SHA224.
- The SHA algorithm field of ICM memory regions has no effect.
- Dual Input Buffer:
- It is recommended to enable double input buffering when higher system bus bandwidth and better performance are required.
- Automatic Monitoring
Mode:
- If monitoring mode is
enabled, the ICM passes through the Main List once to calculate the
message digest of the monitored area and begins monitoring.
- Bus Burden
Control:
- This
field is used to control the burden of the ICM system
bus. The number of system clock cycles between the end
of the current processing and the next block transfer is
set to 2BBC. Up to 32,768 cycles can be
inserted.
Figure 3-4. Bus Burden Control 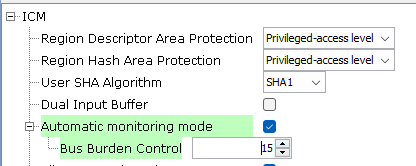
- This
field is used to control the burden of the ICM system
bus. The number of system clock cycles between the end
of the current processing and the next block transfer is
set to 2BBC. Up to 32,768 cycles can be
inserted.
- Bus Burden
Control:
- If monitoring mode is
enabled, the ICM passes through the Main List once to calculate the
message digest of the monitored area and begins monitoring.
- Allow Secondary List:
- Branching to the Secondary List is permitted. Enabled by default.
- Allow End of
Monitoring:
- End of Monitoring is permitted. Enabled by default.
- Allow Write Back:
- Write Back operations are permitted. Enabled by default.
- Only valid if Automatic Monitoring Mode is disabled.
- Number of Regions:
- Number of ICM regions to
use. ICM supports up to 4 non-contiguous memory regions.
Figure 3-5. ICM Regions Selection 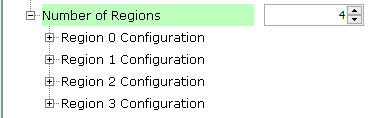
- Bus
Protection:
- Indicates the value of the protection attribute propagated on the system bus when the ICM reads the memory region to be monitored. Possible values are user-access level and privileged-access level.
- SHA
Algorithm:
- Supported SHA algorithms are SHA1, SHA256 and SHA224.
- Processing
Delay:
- When SHA1 algorithm is processed, the runtime period is either 85 or 209 clock cycles.
- When SHA256 or SHA224 algorithm is processed, the runtime period is either 72 or 194 clock cycles.
- Possible values are SHORTEST and LONGEST.
- Interrupts
Configuration:
- Status
Updated Interrupt
- The RSU flag interrupt is set when the corresponding descriptor is loaded from memory to ICM.
- End
Bit Condition Interrupt
- The REC flag interrupt is set when the descriptor with the EOM bit set is processed.
- Wrap
Condition Interrupt
- The RWC flag interrupt is set when the WRAP bit is set in a descriptor of the main list.
- Bus
Error Interrupt
- The RBE flag interrupt is set when an error is reported on the system bus by the bus matrix.
- Digest
Mismatch Interrupt
- The RDM flag interrupt is set when the hash value just calculated from the processed region differs from expected hash value.
- Hash
Completed Interrupt
- The RHC flag interrupt is set when the field NEXT = 0 in a descriptor of the main or second list.
- Status
Updated Interrupt
- Bus
Protection:
- Number of ICM regions to
use. ICM supports up to 4 non-contiguous memory regions.
