RT PolarFire FPGA are provisioned with a set of unique factory keys. In addition, the end users can also enroll their own security keys, thus providing complete independence from using Microchip provided keys. The user encryption key1 (UEK1) and user encryption key2 (UEK2) are user-defined AES-2 symmetric keys. Either of these keys can be used as the root key for encrypting and decrypting bitstreams, and to authenticate them.
To add user security settings in the bitstream:
- 1.In Libero SoC, go to Design Flow > Program Design > Configure Security > Custom security options, as shown in the following figure.Figure 1. Configure Security—Custom Security Options
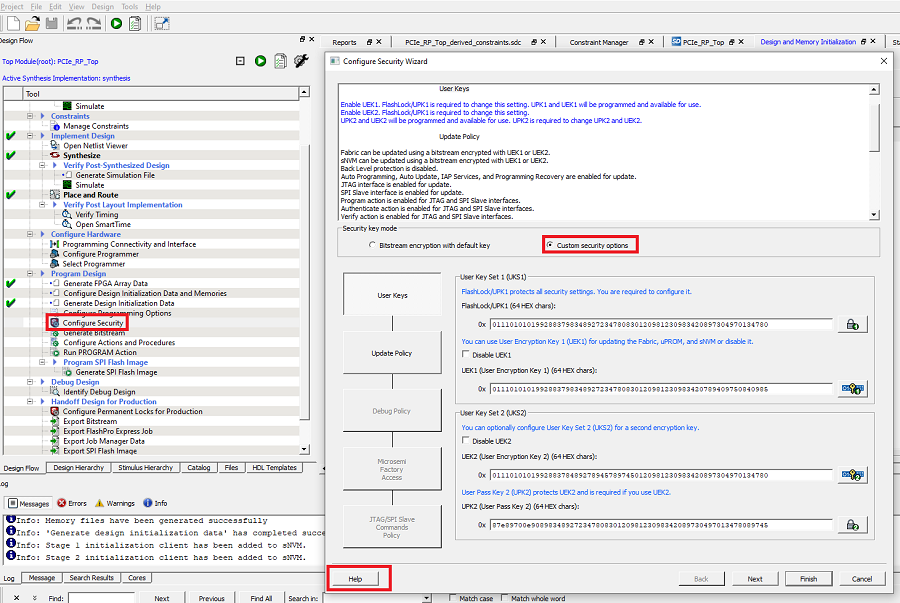
- 2.Click Next to modify Update policy. The Configure Security wizard appears, as shown in the following figure.
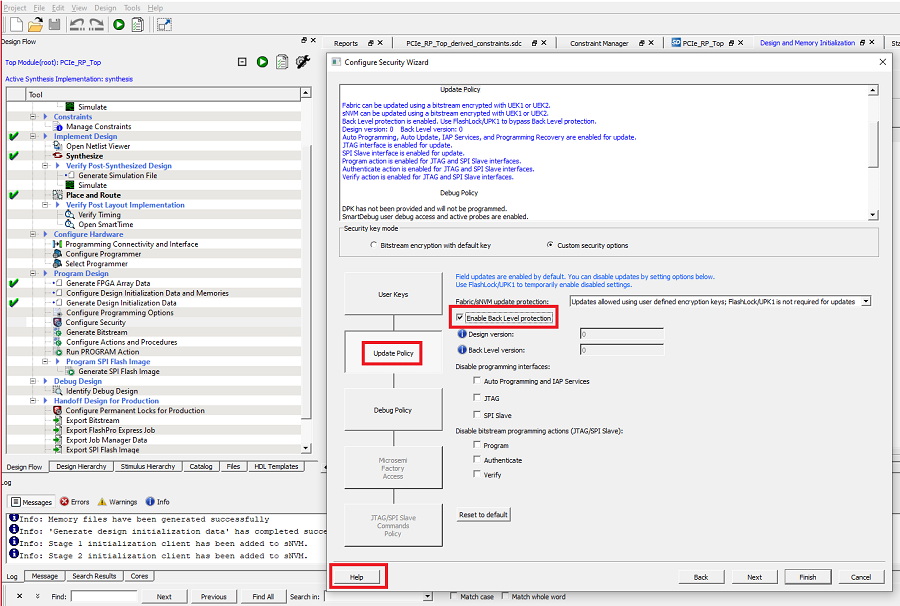
If Back Level protection is enabled, the Back Level version must be lower than the version of the design being programmed. For more information about the fields, click Help. The back-level version value restricts the design version that the device accepts as an update. Only (new) programming bitstreams with a Design Version strictly greater than the current Back Level Version previously stored in the device are allowed for programming. Back-level protection is secured by FlashLock/UPK1, which can be bypassed. The back level version and design version can be modified in the configure programming options tool. For more information about sNVM and security settings, see PolarFire FPGA and PolarFire SoC FPGA Security User Guide.
The following figure shows the configuration of programming options.
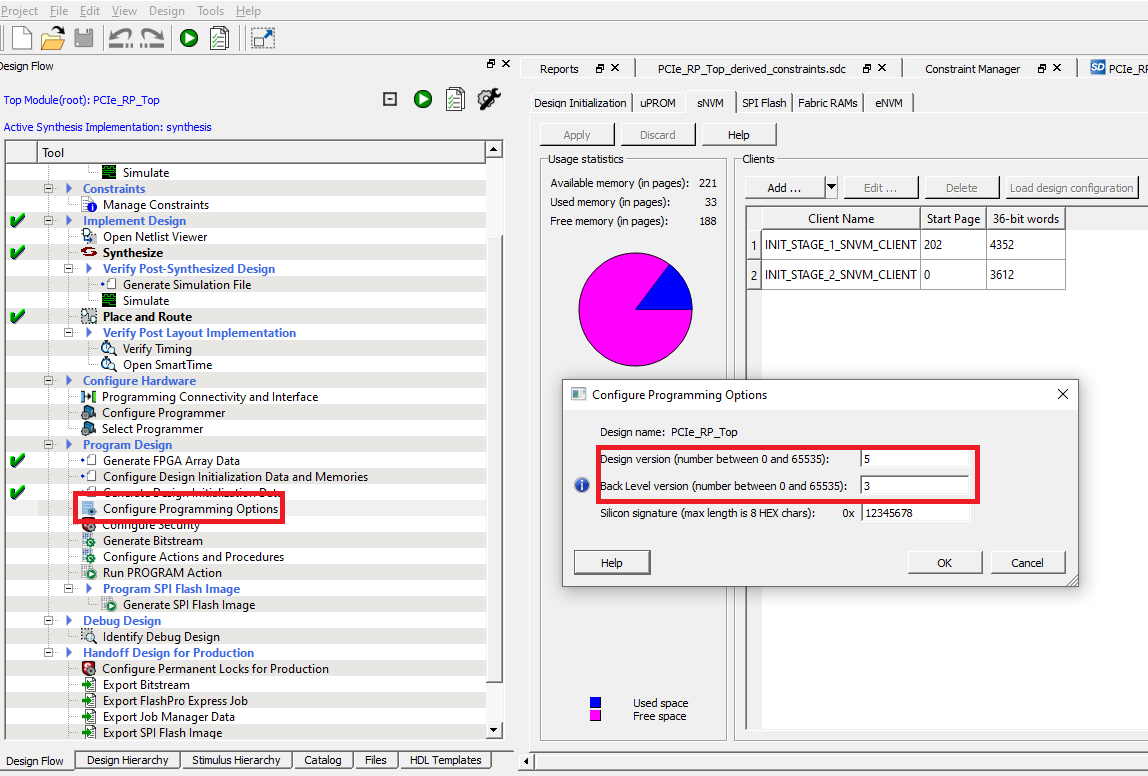
For more information about the bypass back-level protection, see Bypass Back Level Protection Use Case.