1.4 Secure MCC Melody MDFU Client Library – ECDSA Verification Operation Example
This document explains how the Secure MDFU Client authenticates and verifies the incoming application image from the MDFU Host.
The Secure MDFU Client uses the Crypto Authentication Library (CAL) APIs to perform verification on the application either by using the public key stored in bootloader Flash or in a valid key slot of a provisioned secure element. The bootloader verify logic authenticates the image by reading a footer (metadata) from memory, calculating a SHA-256 hash over the specified verification region, and then verifying a digital signature using the secure element and the public key.
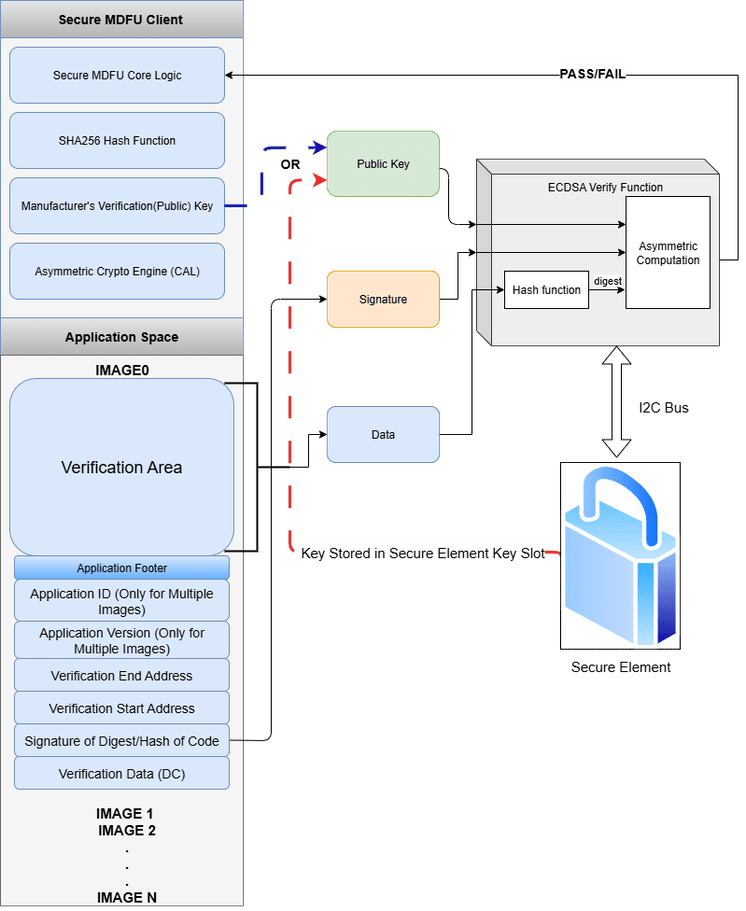
Step-by-Step Breakdown:
- Initialization
- The result of the operation
bl_result_tis set to FAILED by default. - The result of the footer read operation
bl_mem_result_tis set to FAILED by default. - The application footer
structure
bl_footer_data_tto hold the footer data is declared. - A 32-byte sha256Result array for holding the calculated SHA-256 is declared.
- The
ATCA_STATUSStatus flag andisVerifiedflags which are used for signature verification are declared and initialized to false.
- The result of the operation
- Read Application Footer: The
BL_ApplicationFooterRead(&applicationFooter)is called to read the footer data from memory. If the read is successful, the verification operation proceeds; otherwise, it sets result toBL_FAILand returns. - Check Footer Validity: Checks
if the
verificationStartAddressorverificationEndAddressin the footer are not empty. If either of them is empty, the result is set toBL_ERROR_INVALID_ARGUMENTS. - Calculate SHA-256 Hash: Calls
SHA256(applicationFooter.verificationStartAddress, applicationFooter.verificationEndAddress, sha256Result)to compute the hash of the image region - Verify Signature: If the
secure element is provisioned with the public key is, the
atcab_verify_storedCAL API is called to verify the signature using the key stored in a secure element. Otherwise, theatcab_verify_externCAL API is called to verify the signature using the public key stored in bootloader Flash. Both functions setisVerifiedflag toTRUEif the signature is valid. - Set Result Based on
Verification: If signature verification is successful, the
ATCA_STATUSstatus is set toATCA_SUCCESSandisVerifiedisTRUE, which sets the bootloader verification resultbl_result_ttoBL_PASS. Otherwise, the bootloader verification operation resultbl_result_tis set toBL_ERROR_VERIFICATION_FAIL. - Return Result: Returns the final result indicating pass, fail or error
Return Values:
- BL_PASS: Image verification succeeded
- BL_ERROR_VERIFICATION_FAIL: Verification failed (default/fallback)
- BL_ERROR_INVALID_ARGUMENTS: Footer addresses are invalid
- BL_FAIL: Footer could not be read
Summary Table:
| Step | Action |
|---|---|
| Read footer | BL_ApplicationFooterRead |
| Check addresses | Ensure start or end addresses are valid |
| Calculate hash | SHA256 over specified region |
| Verify signature | Use secure element or external public key |
| Return result | Pass, fail or error based on verification outcome |
