1.1.2.1.1.5.6 GAP Security (Encryption) procedure
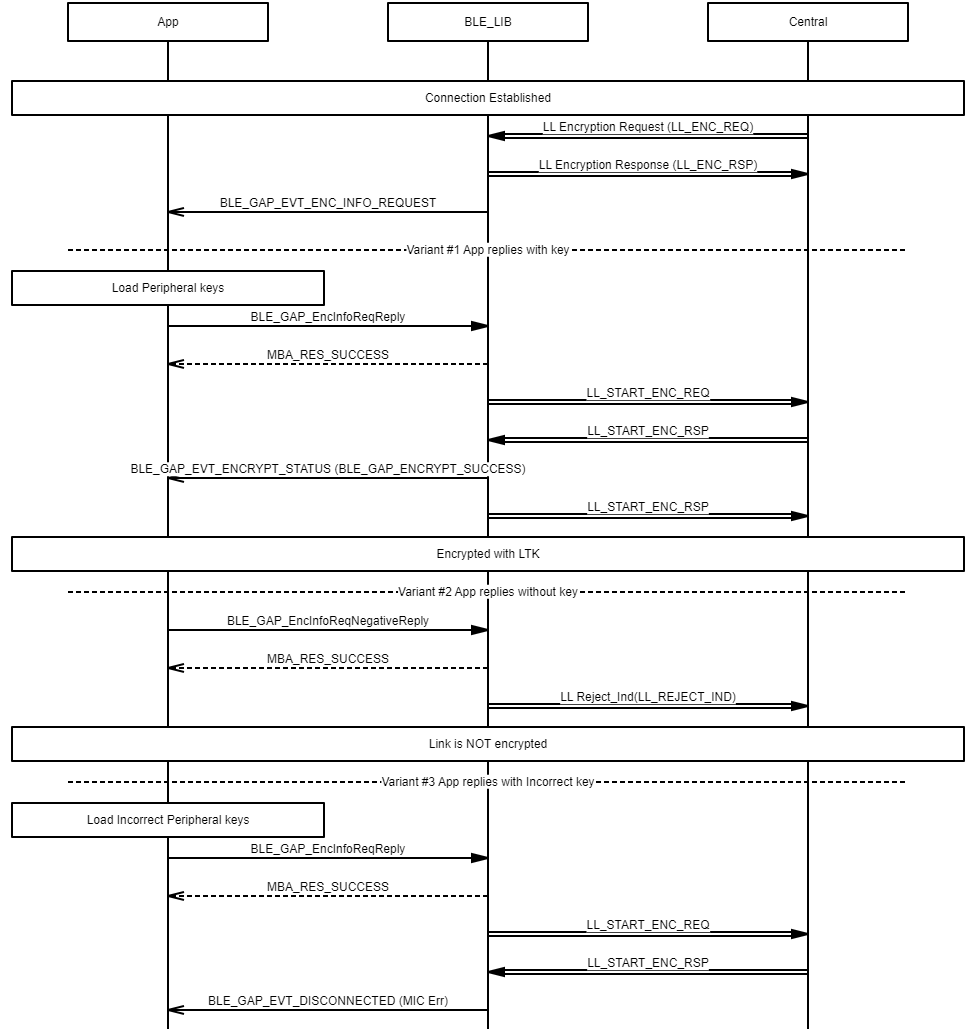
Example of central security (encryption) procedure
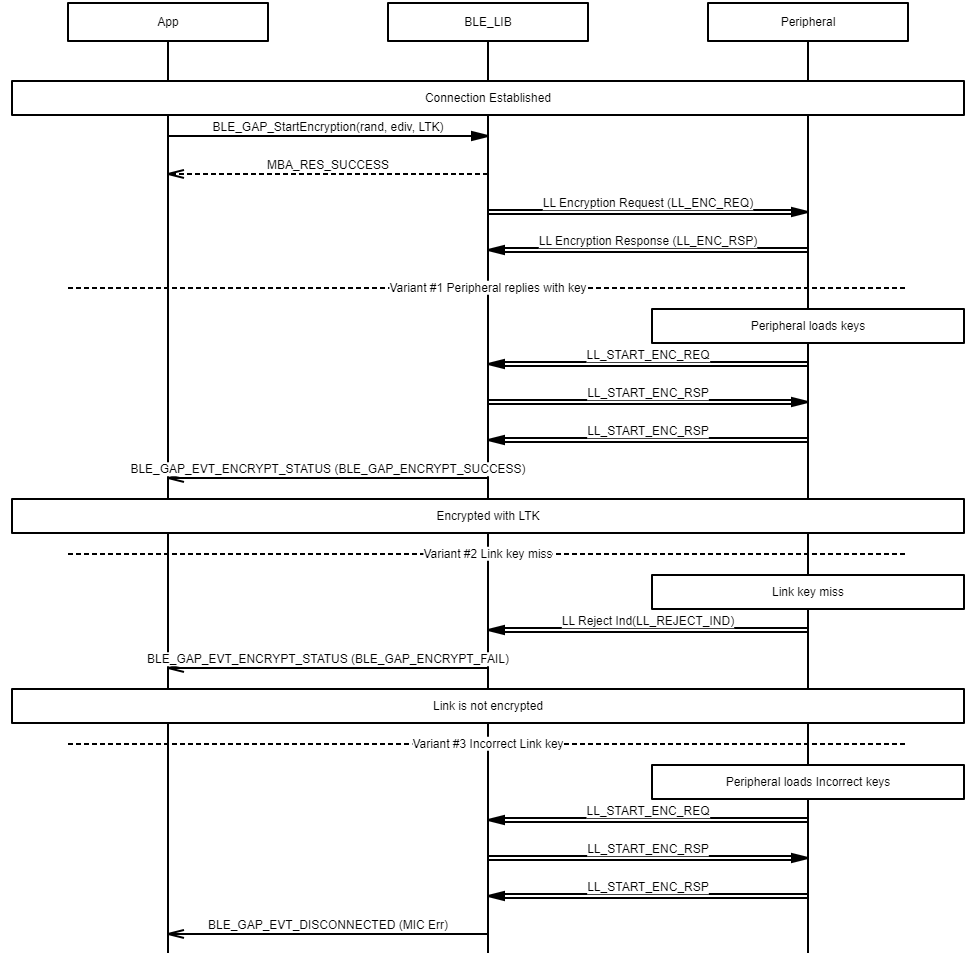
Example of peripheral security (encryption) procedure


The online versions of the documents are provided as a courtesy. Verify all content and data in the device’s PDF documentation found on the device product page.