1.18 TCP/IP WolfSSL TCP Client
This application creates a TCP client with MPLAB Harmony TCP API and establishes a TCP/IP connection to a Web server. The connection can either be clear text, or encrypted connection with wolfSSL.
Description
The TCP/IP WolfSSL TCP Client application is based on MPLAB® Harmony 3 TCP/IP Stack.
The Harmony TCP/IP stack is a collection of different network protocols.
The source files of Harmony 3 TCP/IP stack is available here.
The demo is created with MPLAB X IDE and MCC plugin.
MCC Project Graph - TCP/IP WolfSSL TCP Client
The following Project Graph shows the Harmony components included in the TCP/IP WolfSSL TCP Client demo application.
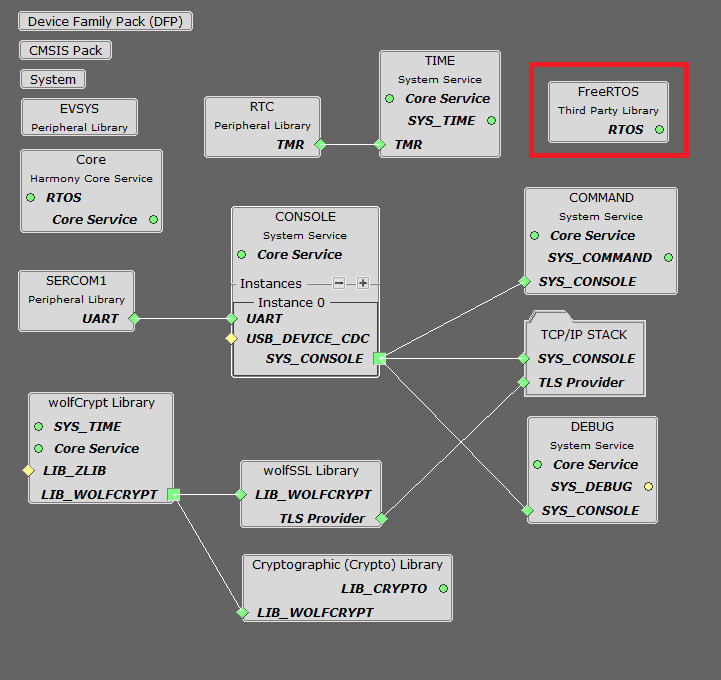
FreeRTOS component is required for RTOS application. For bare-metal (non-RTOS) FreeRTOS component should not be selected.
NOTE - The above diagram contains FreeRTOS component and that is required for RTOS application. For bare-metal(non-RTOS) FreeRTOS component shouldn't be selected.
TCP/IP Configuration - TCP/IP WolfSSL TCP Client
The TCP/IP modules enabled for the demo is shown in the TCP/IP Configuration Overview
More details of TCP/IP Configuration plugin is available here
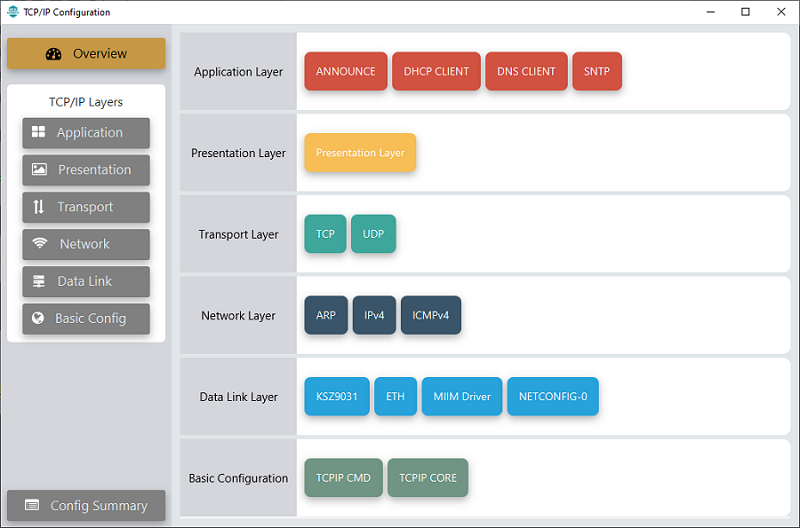
The Application Layer modules enabled in the demo are as follows:
- Application Layer Modules
- ANNOUNCE module to discover the Microchip devices within a local network.
- DHCP Client to discover the IPv4 address from the nearest DHCP Server.
- DNS Client provides DNS resolution capabilities to the stack.
- SNTP Simple Network Time Protocol updates its internal time periodically using a pool of public global time servers.
Downloading and Building the application
To clone or download this application from Github, go to the main page of this repository and then click Clone button to clone this repository or download as zip file.
This content can also be downloaded using content manager by following these instructions.
Path of the application within the repository is apps\wolfssl_tcp_client\firmware .
To build the application, refer to the following list of demo configurations and open the project using MPLAB X IDE.
| Project Name | Target Device | Development Board | Description |
|---|---|---|---|
| pic32cz_ca80_curiosity_ultra.X | PIC32CZ8110CA80208 | PIC32CZ CA80 Curiosity Ultra | TCP/IP WolfSSL TCP Client with KSZ9031 G-bit Ethernet PHY - Bare Metal |
| pic32cz_ca80_curiosity_ultra_freertos.X | PIC32CZ8110CA80208 | PIC32CZ CA80 Curiosity Ultra | TCP/IP WolfSSL TCP Client with KSZ9031 G-bit Ethernet PHY - FreeRTOS |
Hardware Setup
The target board for running the application is PIC32CZ CA80 Curiosity Ultra.
This section provides essential hardware configuration of this target board to run TCP/IP applications.
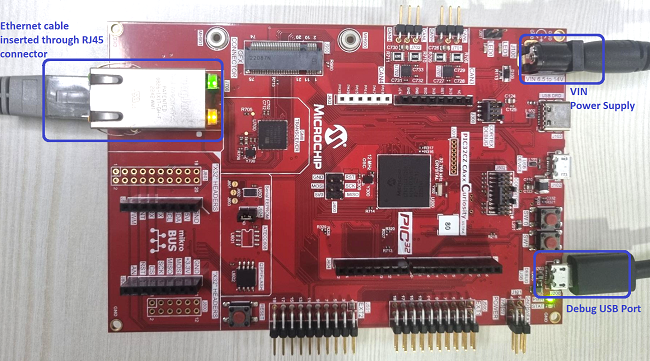
Board Setup
To set up the hardware, refer to the section Board Setup in PIC32CZ CA80 Curiosity Ultra User Guide.
- Connect the power supply ranging from 6.5 to 14V to the VIN port of the PIC32CZ CA80 Curiosity Ultra Evaluation Board.
- Connect the micro USB cable from the computer to the DEBUG USB connector on the PIC32CZ CA80 Curiosity Ultra Evaluation Board.
- Establish a connection between the router/switch with the PIC32CZ CA80 Curiosity Ultra Evaluation Board through the RJ45 connector.
Running the Application
- Open a terminal application on the host computer (like Hyper-terminal or Tera Term).
- Configure the terminal application for serial port connected to USB debug port of the board.
- Set baud rate as 115200 in the terminal application.
- Build and download the application project on the target board.
- Verify the TCP/IP Stack initialization console messages.
Console Start up
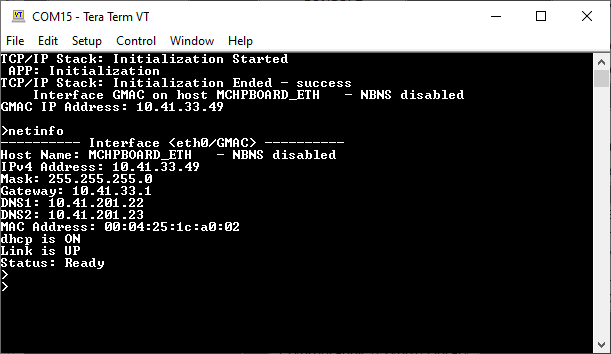
If DHCP client is enabled in the demonstration, wait for the DHCP server to assign an IP address for the development board.
This will be printed on the console. Otherwise, the default static IP address will be assigned to the board.
By entering the command netinfo, the response is obtained as shown above.
TCP Client Test
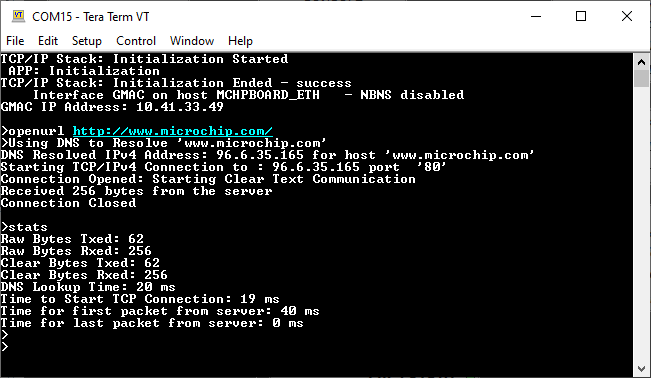
a. Clear text connection (Port 80):
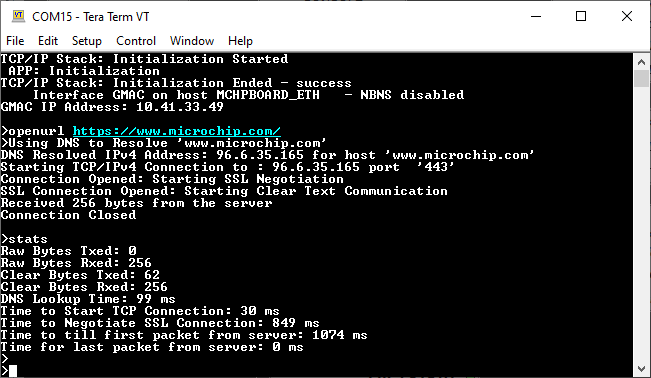
Enter following command in console: openurl <url>. For example, openurl http://www.microchip.com/ , the connection established here is clear text.
By entering the command stats, the response is obtained as shown below.
The response from the server will be printed on the console as shown below.
b. Encrypted connection (Port 443):
Enter following command in console: openurl <url>. For example, openurl https://www.microchip.com/ , the connection established here is encrypted connection with wolfSSL.
The response from the server will be printed on the console as shown below.
By entering the command stats, the response is obtained as shown below.