3.6.2 Software Attack Protection Application on PIC32CM LS00 Curiosity Nano + Touch Evaluation Kit
Description
This application demonstrates safeguarding the PIC32CM LS00 MCU against software attacks using the PIC32CM LS00 Curiosity Nano + Touch Evaluation Kit.
- By leveraging the Boot ROM’s Secure Hash Algorithm 2 (SHA-256) Authentication, the
PIC32CM LS00 can identify unauthorized code fragments in the Non-Secure Memory and
replace them with an authentic version of the Non-Secure firmware.
Modules/Technology Used
-
Peripheral Modules
- SERCOM3 (USART)
- RTC
- EIC
- SYSTICK
- Power Manager (PM)
- EVSYS
- NVMCTRL
- PORT
-
System Services
- STDIO
Hardware Used
Software/Tools Used
This project has been verified to work with the following versions of software tools:
Refer Project Manifest present in harmony-manifest-success.yml under the project folder firmware/src/config/default
- Refer the Release Notes to know the MPLAB® X IDE and MCC Plugin version. Alternatively, Click Here.
Because Microchip regularly update tools, occasionally issue(s) could be discovered while using the newer versions of the tools. If the project doesn’t seem to work and version incompatibility is suspected, It is recommended to double-check and use the same versions that the project was tested with.
To download original version of MPLAB® Harmony v3 packages, refer to document How to Use the MPLAB® Harmony v3 Project Manifest Feature (DS90003305).
Hardware Setup
- Connect the PIC32CM LS00 Curiosity Nano + Touch Evaluation Kit to the Host PC as a USB
Device through a Type-A male to micro-B USB cable connected to Micro-B USB (Debug USB) port
Programming hex file
The pre-built hex file can be programmed by following the below steps.
- Open MPLAB X IDE
- Close all existing projects in IDE, if any project is opened.
- Go to File -> Import -> Hex/ELF File
- In the Import Image File window,
- Create Prebuilt Project,
- Click the Browse button to select the prebuilt hex file.
- Select Device as PIC32CM5164LS00048.
- Ensure the proper tool is selected under Hardware Tool and click on Next button.
- Select Project Name and Folder,
- Select appropriate project name and folder and click on Finish button
- Create Prebuilt Project,
- In MPLAB X IDE, click on Make and Program Device button to program the device.
- Follow the steps in Running the Demo section below.
Programming/Debugging Application Project
- Open the project group (pic32cm_ls00_software_attack_protection/firmware/tz_pic32cm_ls00_cnanogroup) in MPLAB® X IDE
- Right click on tz_pic32cm_ls00_cnanogroup file and go to Open Required projects > Open All Projects.
- Then right click on the non-secure project and click Set as Main Project.
- Ensure PIC32CM LS00 Curiosity Nano is selected as hardware tool to program/debug the application
- Build the code and program the device by clicking on the make and program button in MPLAB X IDE tool bar
- Follow the steps in Running the Demo section below.
Running the Demo
- After building the application and completing the programming, open the MPLAB® Data
Visualizer by clicking the highlighted icon below.
- Configure the serial port setup of the PIC32CM LS00 Curiosity Nano + Touch Evaluation
Kit by clicking the Gear icon shown below.
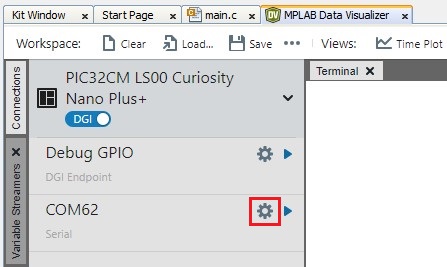
- Set the 115200 as baudrate in the COM setting.
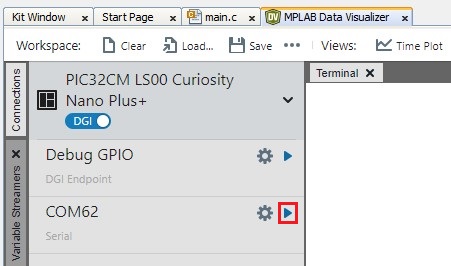
- Open the Serial Port of the PIC32CM LS00 Curiosity Nano + Touch Evaluation Kit by
clicking the Play icon as follows.
- Select the Sent to Terminal to view the serial console message and click Close.
-
Open the command prompt and navigate the following location.
Path: C:/Program Files/Microchip/MPLABX/v6.20/mplab_platform/mplab_ipe
Important: The PIC32CM LS00 Curiosity Nano + Touch Evaluation Kit has no RESET button to reset the MCU. To reboot the board, the RESET command is sent to the nEDBG to reset the MCU with the help of MPLAB® IPECMD. -
Run the following command to reset the PIC32CM LS00 Curiosity Nano + Touch Evaluation Kit.
ipecmd.exe -P32CM5164LS00048 -TPNEDBG -OK
- Observe the startup console message on the MPLAB® Data Visualizer and the LED1 will toggle on the PIC32CM LS00 Curiosity Nano + Touch Evaluation Kit
- Press the SW1 button on the PIC32CM LS00 Curiosity Nano + Touch Evaluation Kit to simulate a software attack
- Observe the console message of software attack initiation on the MPLAB® Data Visualizer
Comments
- Reference Training Module: Arm TrustZone Getting Started Application on PIC32CM LS60 (Arm Cortex-M23) MCUs
- This application demo builds and works
out of box by following the instructions above in Running the Demo section. If the
user needs to enhance/customize this application demo, should use the MPLAB Harmony v3
Software framework. Refer links below to setup and build the applications using MPLAB
Harmony.
- How to Setup MPLAB Harmony v3 Software Development Framework (DS90003232).
- How to Build an Application by Adding a New PLIB, Driver, or Middleware to an Existing MPLAB Harmony v3 Project (DS90003253).
- How to Set up the Tools Required to Get Started with MPLAB® Harmony v3 and MCC
- Create a new MPLAB Harmony v3 project using MCC
- Update and Configure an Existing MHC-based MPLAB Harmony v3 Project to MCC-based Project
