1.2.1.19.1 Abstraction Model
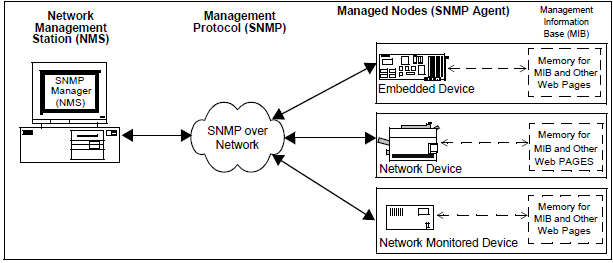
SNMP Server (Agent)
SNMP is an Internet protocol that was originally designed to manage different network devices, such as file servers, hubs, routers, and so on. It can also be used to manage and control an ever increasing number of small embedded systems connected to one another over any IP network. Systems can communicate with each other using SNMP to transfer control and status information, creating a truly distributed system
Location of the SNMP Stack in the TCP/IP Protocol Stack:
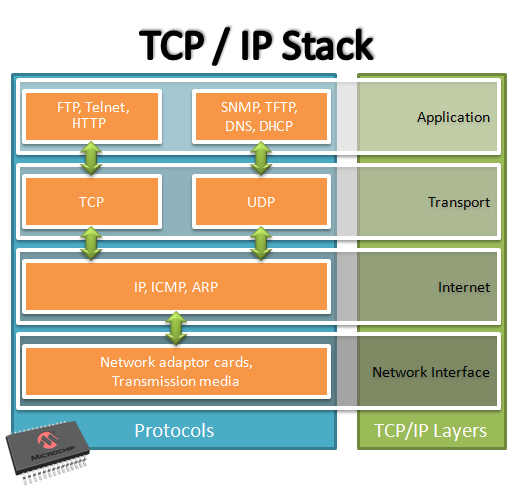
The Microchip SNMP Server is a multi-lingual implementation, which supports SNMPv1, V2c, and V3 server features simultaneously. The SNMP Server is implemented to address the requirements of embedded applications and works with both IPv4 and IPv6 addresses. SNMPv1 and V2c are enabled by TCPIP_STACK_USE_SNMP_SERVER. SNMPv3 support is enabled by TCPIP_STACK_USE_SNMPV3_SERVER. Since the SNMPv3 stack requires the support of SNMPv1 and SNMPv2c, TCPIP_STACK_USE_SNMPV3_SERVER should be enabled with TCPIP_STACK_USE_SNMP_SERVER.
V2c
V2c is implemented with support for the configuration of multiple community names and the community names can be configured through the HTTP web interface. An access-restricted web page is provided with the demonstration application to allow dynamic configuration of SNMP communities.
SNMPv3
SNMPv3 RFC specifies different types of access mechanisms, user security model (USM), authentication and privacy protocols. The Microchip SNMPv3 Server is implemented with support for the AES 128 CFB 128 and DES-CBC privacy protocols, and the MD5 and SHA1 message authentication protocols. The demonstration implementation of the server is configured with three types of user names with respective authentication and privacy credentials and authentication types. These credentials and other user information are stored in the global array. The user of the SNMPv3 stack can decide on the number of user names in the User’s database to be stored with the SNMPv3 Server. According to the SNMPv3 recommendation, the SNMPv3 Server should not be configured with the authentication and privacy passwords. Instead, it could be configured with the respective localized keys of the password. The Microchip SNMPv3 agent is provided with the password information in the database for "Getting Started" and for understanding purposes only. It is recommended that the SNMPv3 stack be modified to restrict access to the password OIDs declared in the user database.
MIB Files
SNMP describes the hierarchal storage of management objects (referred to with object IDs or OIDs) with MIB files. The Microchip SNMP server demonstration includes two MIB files:
mchip.mib - This is an Abstract Syntax Notation One (ASN.1) formatted MIB file containing information about the variables used in the demonstration
snmp.mib - This is a custom-formatted file that can be parsed to create Web page and header resources that can be accessed with a MCHP device
The TCP/IP Stack includes the mib2bib utility, which will compile the custom Microchip MIB script (snmp.mib) to generate two files named snmp.bib and mib.h. The snmp.bib file is a compressed record of management objects that will be stored with web pages and the mib.h file contains C defines for each OID. These files are included in the appropriate directories for the TCP/IP Demonstration Applications, but for a custom application the snmp.bib must be copied to the web page directory, mib.h copied to the application directory and included in the project. Rebuild your project, and then rebuild and re-upload the web page. This will bundle the BIB file into the web page image, which will allow the SNMP agent to search for the required variable information with the MPFS file system.
MIB Browsers
Several SNMP MIB browsers are available. Users can also install a customized MIB browser specific to their application.
This documentation describes how to use the iREASONING Networks MIB Browser to run the TCP/IP SNMP demonstration applications. The MIB Browser can be obtained from: http://www.ireasoning.com/downloadmibbrowserlicense.shtml. The MIB script upload, the MIB tree structure display, and the SNMP query mechanism procedures vary from browser to browser.
Refer to the Microchip application note, AN870 "SNMP V2c Agent for Microchip TCP/IP Stack" (DS00000870) for more details on the MIB scripts, community names, and demonstration SNMP MIB variable tree structure.
The ASN.1 format mchip.mib file is defined with a private variable tree structure for the MIB variables. Also the mchip.mib is added with the number of OIDs that could be accessed only with SNMPv3 request. The browser can access every variable in the MIB database provided the community name matches. The access to the MIB variables is restricted to the type of the request. The RFC1213 MIB variables could be accessed with SNMPv2c/v3 request. But the SNMP-FRAMEWORK-MIB.mib variables could only be accessed with a SNMPv3 request if the credentials are matched and the message is authenticated. To modify these MIB variables, corresponding changes must be made to both MIB scripts (snmp.mib and mchip.mib).
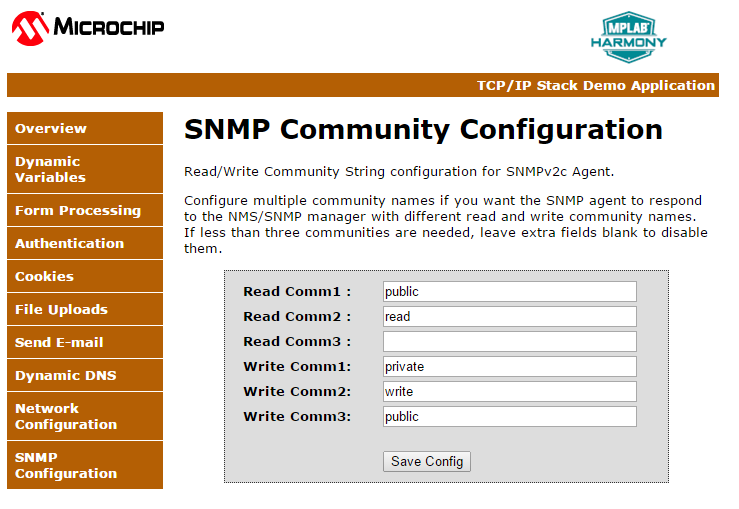
- For SNMP V2c services , The V2c agent is configured by default with three Read communities ("public", "read", "") and three Write communities ("private","write","public")
- At run-time, the community names can be dynamically configured using the HTTP interface for SNMP community name configuration
- If the V2c agent receives an SNMP request with an unknown community name, the agent will generate an Authentication trap
The V2c agent's multiple community support feature enables the user application to provide limited access to the requesting browser based on the community name used by the browser to access the MIB database variables of the agent.
For SNMPv3 services:
| Type | USER 1 | USER 2 | USER 3 |
|---|---|---|---|
| USM User | microchip | SnmpAdmin | root |
| Security Level | auth, priv | auth, no priv | no auth, no priv |
| Auth Algorithm | MD5 | SHA1 | N/A |
| Auth Password | auth12345 | ChandlerUS | N/A |
| Privacy Algorithm | AES | N/A | N/A |
| Privacy Password | priv12345 | N/A | N/A |
If SNMPv3 services are required, SNMPv3 browser is required to be configured with the user name, authentication and privacy password, message authentication hash type, privacy protocol type. The SNMP server would respond only if one of the user credentials and user security parameters in the following table is configured at the manager. The previous table is stored in the global structure with the SNMPv3 server stack. The SNMPv3 server would only respond if the request credentials of the MIB browser matches to that of the stored user data base of the SNMP server.
The Microchip SNMPv3 stack does support only one Context Engine ID with the server. Leave the "Context Name" option in the "Advanced" tab empty. It is ignored on the server.
According to the user and the auth and privacy protocols configured with the SNMP browser, the UDP authenticated and encrypted message would be exchanged between server and the client.
- If the USER 1 values, as shown in the table, are configured in the MIB browser, the data exchange between the client and server is encrypted and authenticated. The PDU could be captured in the Ethernet packet sniffer, such as WireShark, and examined. As the data is encrypted and authenticated, the data integrity and the privacy is achieved.
- If USER 2 values, as shown in the table, are configured in the MIB browser, the data exchange between client and server is authenticated. The data integrity would be checked once the data is received at either end. The message authentication mechanism protects from the possible data sniffing and modification threat, and also guarantees that the data is received from the authenticated and guaranteed source.
- If USER 3 values, as shown in the table, are configured in the MIB browser, the data exchange between client and server is neither authenticated nor encrypted
- Considering the three USER configurations, if the SNMP server is to be accessed over WAN, in the Internet cloud, the data should be encrypted and authenticated to have the highest level of data privacy and integrity
SNMP Traps
The MPLAB Harmony TCP/IP Stack supports Trap version1 and Trap version2 formatted traps. Traps are notifications from the agent to the manager that are used when a predefined event occurs at the agent.
From mchip.mib, the ipv4TrapTable and ipv6TrapTable are the two tabular sections, which are used to configure HOST IPv4 and IPv6 address and this will help the HOST trap receiver to receive the traps.
Several preprocessor macros in the snmp_config.h variant header file can be used to enable or disable traps in the agent. Commenting and uncommenting these macros in the file will have different results. The SNMP_TRAP_DISABLED macro will disable traps entirely if it is not commented:
#define SNMP_TRAP_DISABLED#define SNMP_STACK_USE_V2_TRAPIf the macro has been commented out, the SNMP agent will send V1 formatted trap PDUs; otherwise, it will send V2 formatted trap PDUs. By default, the SNMP agent is configured to send V2 formatted traps. Note that the SNMP V2c agent should only send V2 formatted traps.
To enable traps in SNMPv3, the #define SNMP_V1_V2_TRAP_WITH_SNMPv3 macro must be uncommented.
The following table illustrates how to enable/disable traps for different versions of SNMP.
| Type | SNMPv1 | SNMPv2c | SNMPv3 |
|---|---|---|---|
| TRAPv2 (enabled by default) | Comment out the #define SNMP_TRAP_DISABLED macro | Comment out the #define SNMP_TRAP_DISABLED macro | Comment out the #define SNMP_TRAP_DISABLED macro. Uncomment the #define SNMP_V1_V2_TRAP_WITH_SNMPV3 macro |
| TRAPv2 (disabled by default) | Not supported | Comment out the #define SNMP_TRAP_DISABLED macro. Uncomment the #define SNMP_STACK_USE_V2_TRAP macro | Comment out the #define SNMP_TRAP_DISABLED macro Uncomment the #define SNMP_V1_V2_TRAP_WITH_SNMPV3 macro. Uncomment the #define SNMP_STACK_USE_V2_TRAP macro |
Demonstrations
Two trap demonstrations APIs are included with the TCP/IP Stack. The task functions for these demonstrations are called in the main application function:
- SNMPTrapDemo - This API demonstrates V1 or V2 trap formats (depending of the status of the SNMP_STACK_USE_V2_TRAP macro). The trap PDU will only have one demonstration variable binding on the varbind list.
- SNMPV2TrapDemo - This API provides V2 format notifications with multiple (4) variable bindings. The user should modify or use this routine as a reference for sending V2 trap format notifications with multiple bindings on the varbind list.
V1/V2 Formatted Traps with a Single Variable Binding
In the snmp_config.h header file:
- Uncomment #define SNMP_TRAP_DISABLED
- Comment //#define SNMP_STACK_USE_V2_TRAP
For the Trap demonstration, two events are defined within the V2c agent:
- If the Analog Potentiometer value is greater than 14, the agent will send a Trap every 5 seconds to the configured 'IPv4TrapReceiverIP address'.
- If Button 3 on the demonstration board is pressed, an organization-specific PUSH_BUTTON trap will be sent.
The current implementation of the V2c agent also generates a standard "Authentication Failure Trap":
- If a request is received to modify (Set) a private MIB variable, or
- If the value of the variable is requested (Get) by a browser with the wrong community name
HTTP Configuration
If a HTTP server is used with the Harmony TCP/IP stack, it is possible to dynamically configure the Read and Write community names through the SNMP Configuration web page. Access the web page using http://mchpboard_c/mpfsupload or http://<Board IP address>(for IPv6 it should be http://[Ipv6 address]:80/index.html), and then access the SNMP Configuration web page through the navigation bar. Use "admin" for the username and "microchip" for the password.