5.3 Checksum
In this method the application image will be verified by calculating a checksum on the
application space and comparing the result to a pre-calculated checksum in the bootloader.
To learn more about checksum, read this reference.
Overview
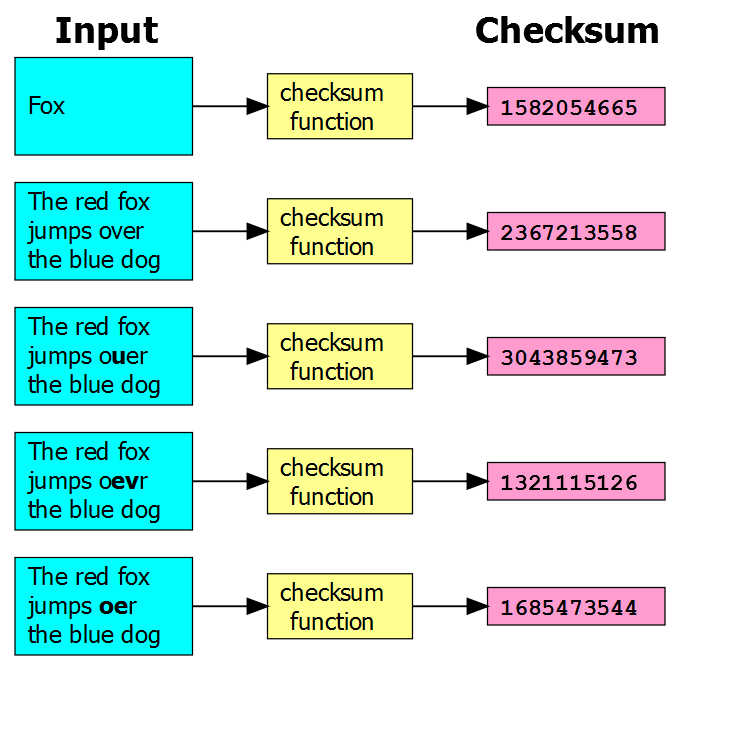
Checksum verification is a method used to validate the integrity of the bytes present in a given memory range through a direct mathematical analysis. A memory range is given to a checksum function where a special value called a checksum is calculated from the data that is present in the given memory range and then that value is compared to the checksum calculated by the bootloader during the programming step. If both checksum values match then there is a very high probability the data has not been accidentally altered or corrupted. This method is only capable of detecting errors in transmission or storage and it is unable to perform authenticity checks on the data’s source.
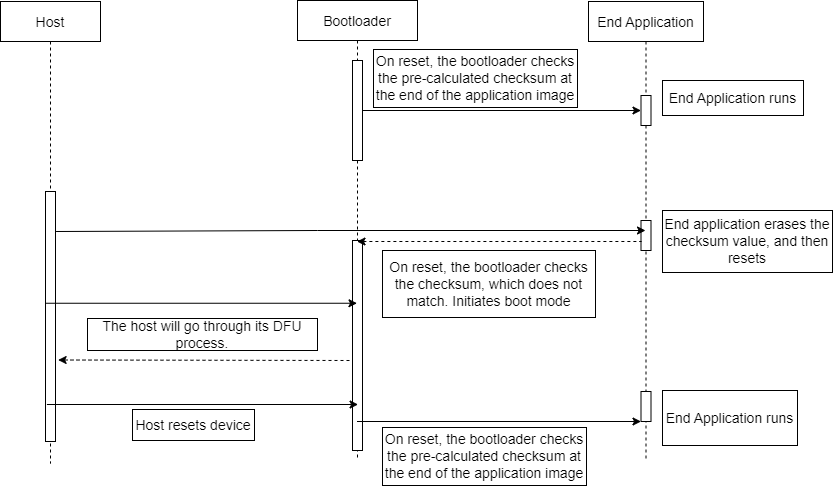
Verification Flow
In Checksum verification, the bootloader has a very simple program flow for the verification steps. On a normal start-up, the bootloader will simply perform a checksum calculation on the program memory space and compare that value to the pre-calculated checksum that resides in the bootloader from the original calculation that occurs at the device programming step. On a device reset, application space is first cleared, this will force a failure in the verification steps which is then caught by the bootloader. From there the bootloader starts the device programming process and calculates the new checksum on the application hex file like a normal execution would. After the device programming has finished the bootloader will calculate another checksum on the application memory space and compare that new value to the pre-calculated one from the programming step. If the checksum values match it is verified that the data present in the program memory is the valid Hex file from the application code and the data’s integrity has not been compromised during transmission. This method, again, is unable to perform source authenticity checks.