2.4.2 Execution Flow
Secure Firmware Execution Flow
The following figure illustrates the system-level execution flow of Secure firmware in the Software Attack Protection application.
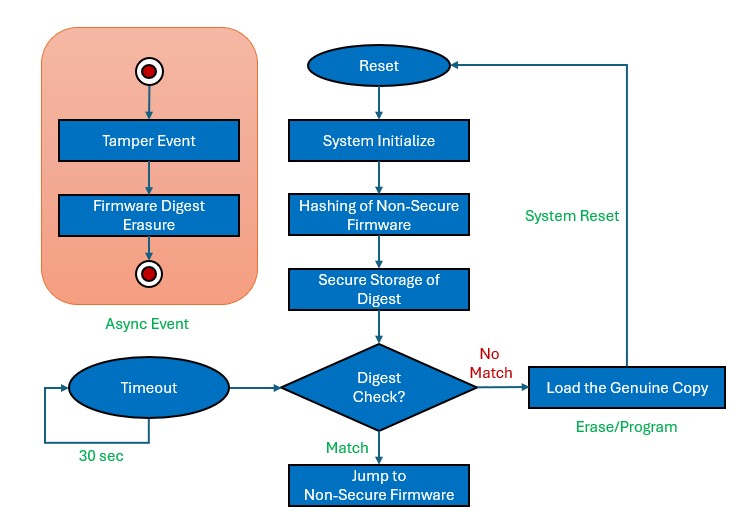
The Secure application executes in the following sequence:
- After a system reset, the application initiates the Non-Secure firmware hashing process to generate a firmware digest.
- The calculated digest is stored in the data Flash memory within the Secure region.
- The firmware digest of the Non-Secure application is verified against the genuine copy in the Secure Flash memory.
- Upon successful verification, the execution is jumped to the Non-Secure application.
- If verification fails, the Non-Secure application is erased, and the genuine copy is loaded into the Non-Secure Flash region.
- Every 30 seconds, the firmware digest is regenerated and cross-verified with the genuine copy to ensure authenticity.
Non-Secure Firmware Execution Flow
The following figure illustrates the system-level execution flow of Non-Secure firmware in the Software Attack Protection application.
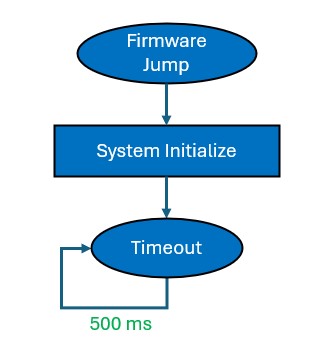
The Non-Secure application executes in the following sequence:
- After a firmware jump from the Secure application, the Non-Secure firmware initializes the Non-Secure peripherals.
- Toggles the LED1 for every 500 millisecond on the PIC32CM LS00 Curiosity Nano+ Touch Evaluation Kit.
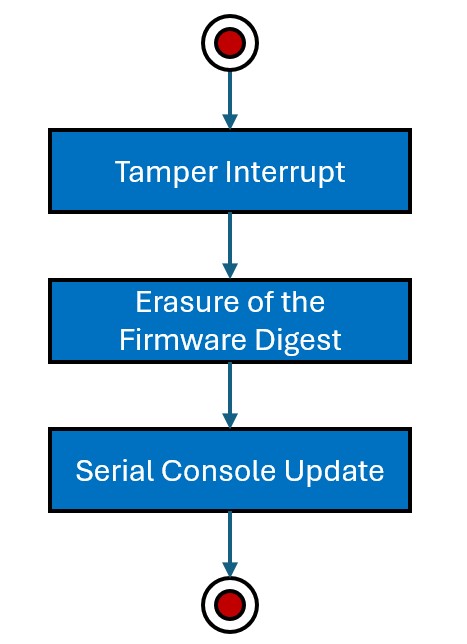
Software Attack Simulation Execution Flow
The simulation of a software attack is conducted in the following sequence:
- Pressing the SW1 button on the PIC32CM LS00 Curiosity Nano+ Touch Evaluation Kit simulates a software attack by triggering a tamper event.
- Following the tamper event, the RTC initiates the data Flash content erasure process.
- Within the RTC tamper handler, a message indicating the initiation of the software attack is sent to the serial console.
The following figure illustrates the system-level execution flow of Software Attack in the Secure firmware.