4.1 Adding the Non-Secure Application Logic
To develop and run the application, follow these steps:
- Open the
main.cfile of the Non-Secure project (tz_pic32cm_ls00_cnano.X) and add the following code after the SYS_Initialize():SYSTICK_TimerStart(); - Inside the while loop, add the
following code to toggle the LED at a default rate of 500
ms:
LED_Toggle(); SYSTICK_DelayMs(500); - Go to the Non-Secure Project Properties, and enter the post-build command for
generating a Non-Secure firmware genuine copy:
- In the MPLAB X IDE Project Properties window perform these actions.
- Under the left Categories section, select Building and in the right Configuration properties page, select the Execute this line after build check box.
- Enter the following post
command below the check
box.
rm -rf ${ProjectDir}/../../hex && mkdir ${ProjectDir}/../../hex&& cp ${ProjectDir}/${ImageDir}/*.hex ${ProjectDir}/../../hex && ${MP_CC_DIR}"/xc32-objcopy" -I ihex -O binary ${DISTDIR}/${PROJECTNAME}.${IMAGE_TYPE}.hex ${DISTDIR}/${PROJECTNAME}.${IMAGE_TYPE}.bin && cp ${ProjectDir}/${ImageDir}/*.bin ${ProjectDir}/../../hex
Figure 4-1. Generating The Non-Secure Firmware Genuine Copy 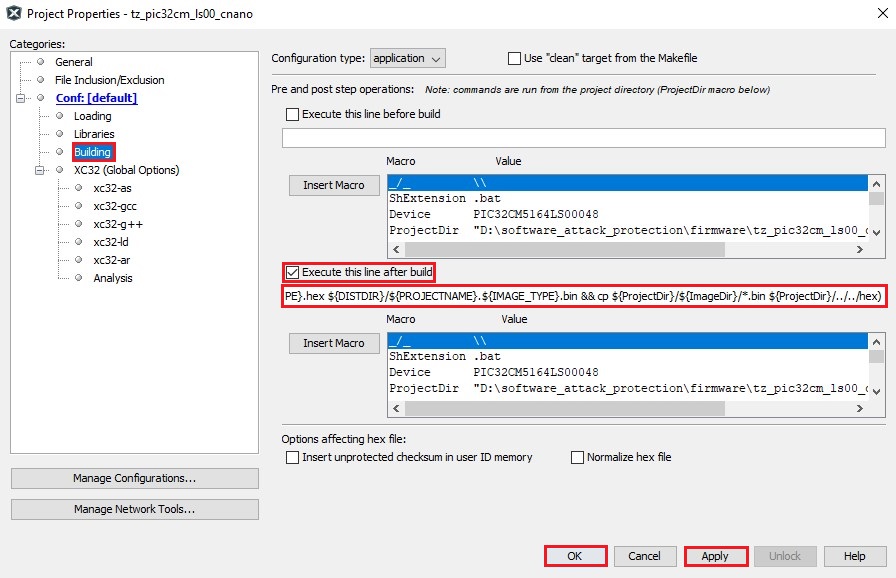
- Click Apply, and then click OK.
- Under Projects, right-click on the
tz_pic32cm_ls00_cnano and then select Set as Main Project.
Figure 4-2. Make the Non-Secure Project as Main Project 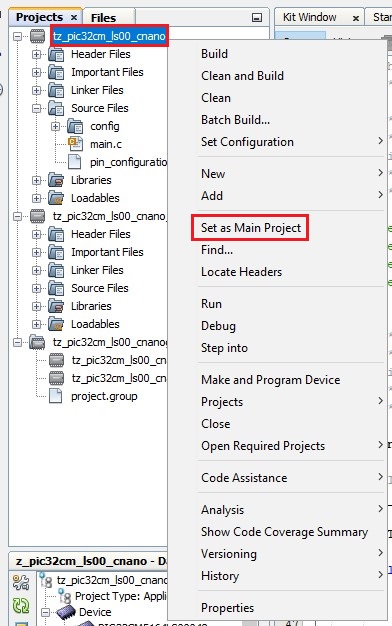
- Build the project by clicking the
Clean and Build icon or by selecting Clean and Build Main Project
from the drop-down list and verify that the project builds successfully.
Figure 4-3. Clean and Build 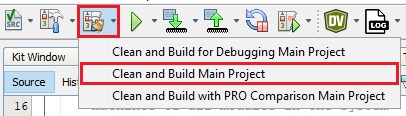
- Check if the binary file of the
Non-Secure project is available in the hex folder location (path:
D:/software_attack_protection/hex).
Figure 4-4. Location of Generated Binary File 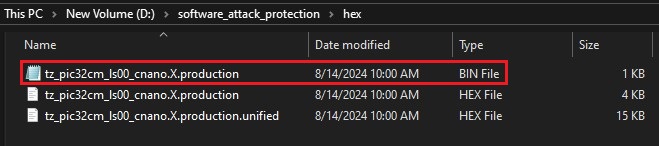
- Open the command prompt and navigate
to the following location.
Path: <Harmony folder path>/ bootloader/tools
Note: If the bootloader folder is not found inside the Harmony folder, download the bootloader package (v3.7.0 or above) using the MPLAB Content Manager. - Run the python script
btl_bin_to_c_array.pyto convert the Non-Secure application binary file to a C-style array containing Hex output.python btl_bin_to_c_array.py -b D:\software_attack_protection\hex\tz_pic32cm_ls00_cnano.X.production.bin -o D:\software_attack_protection\firmware_secure\src\non_secure_app_image_pic32cm_ls00_cnano.h -d PIC32CMFigure 4-5. Running the Python Script 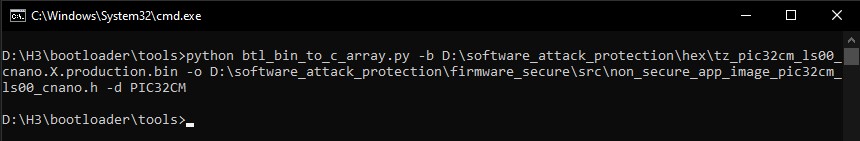
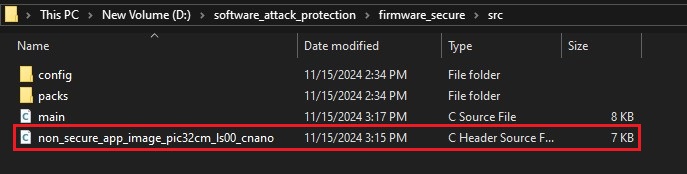
- Once the script is successfully executed, a header file of the Non-Secure
Application Image (Genuine Copy) is found in the source folder of the Secure
Project.
Figure 4-6. Genuine Copy of the Non-Secure Application Image