15.2.6.1 Main SPPS Flow
(Ask a Question)The main objectives of this flow are to support secured programming of a blank device (initial programming), enforce overbuild protection, and allow an upgrade flow for already-programmed devices.
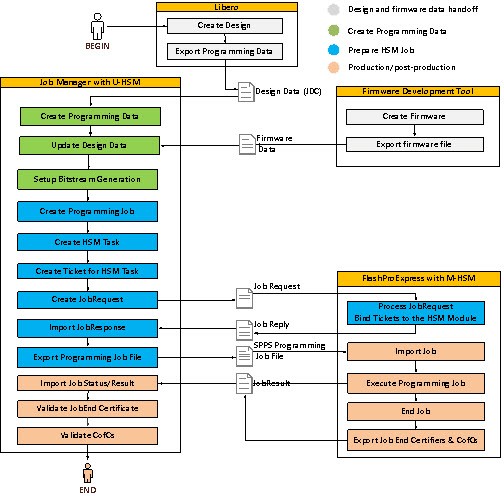
In this flow, all user-selected design information such as Fabric, eNVM, and Security is exported from Libero through a JDC file and handed off to the OE, which uses the Job Manager to create and submit an HSM Programming Job for production. The eNVM client data can be updated in the Job Manager during this step.
All operations related to generation and use of encryption keys, pass keys, and other protected data is handled by the User HSM (U-HSM). Production executes the received HSM Programming Jobs using FlashPro Express. The Manufacturer HSM (M-HSM) serves FlashPro Express security protocol requests, and enforces the overbuild protection policy. Proof of programming results such as Certificates of Conformance generated by the programmed devices and the job end certifiers are sent back to the OE and can be validated using the U-HSM.
From a design security standpoint, design and operation areas are always considered to be trusted environments. OE can modify security settings from Libero through the JDC file. Production in the main (HSM-based) SPPS flow is considered an untrusted area with respect to design, security, and job execution. The following figure shows the main SPPS flow for programming.
In the SmartDebug flow, all user-selected design information such as Fabric, eNVM, and Security is exported from Libero through a JDC file and handed off to the OE, which uses the Job Manager to create and submit an HSM Debug Job for production.
All operations related to generation and use of encryption keys, pass keys, and other protected data is handled by the User HSM (U-HSM). Production executes received HSM Debug Jobs using SmartDebug. The Manufacturer HSM (M-HSM) serves SmartDebug security protocol requests and enforces the overbuild protection policy. From a design security standpoint, design and operation areas are always considered to be trusted environments. OE can modify security settings from Libero through the JDC file. Production in the main (HSM-based) SPPS flow is considered an untrusted area with respect to design, security, and job execution. The following figure shows the main SPPS flow for SmartDebug.
