43.3.6.11 Generating an ECDSA Signature (Compliant with FIPS 186-2)
Purpose
This service is used to generate an ECDSA signature following the FIPS 186-2. It performs the second step of the Signature Generation. A hash value (HashVal) must be provided as input, it has to be previously computed from the message to be signed using a secure hash algorithm.
A scalar number must be provided too as described in the FIPS 186-2. The result (R,S) is computed by this service.
How to Use the Service
Description
The operation performed is:
(R, S) = EcDsaSign(PtA, HashVal, k, CurveParameters, PrivateKey)
This service processes the following checks:
- If the Scalar Number k is out of the range [1, PointOrder -1], the calculus is stopped and the status is set to PUKCL_WRONG_SELECT_NUMBER.
- If R equals zero, the calculus is stopped and the status is set to PUKCL_WRONG_SELECT_NUMBER.
- If S equals zero, the calculus is stopped and the status is set to PUKCL_WRONG_SELECT_NUMBER.
In this computation, the following parameters need to be provided:
- A the input point is filled in “mixed” coordinates (X,Y) with the affine values and Z = 1 (pointed by {nu1PointABase,3*u2ModLength + 12})
- Cns the working space for the Fast Modular Constant not initialized (pointed by {nu1CnsBase,u2ScalarLength + 8})
- P the modulus filled (pointed by {nu1ModBase,u2ModLength + 4})
- The workspace not initialized (pointed by {nu1WorkSpace, 8*u2ModLength + 44}
- The a parameter relative to the elliptic curve (pointed by {nu1ABase, u2ModLength + 4})
- The order of the Point A on the elliptic curve (pointed by {nu1OrderPointBase, u2ScalarLength + 4})
- k the input Scalar Number beforehand generated and filled (pointed by{nu1ScalarNumber,u2ScalarLength + 4})
- HashVal the hash value beforehand generated and filled (pointed by {nu1HashBase, u2ScalarLength + 4})
- The Private Key (pointed by {nu1PrivateKey, u2ScalarLength +4})
- Generally, u2ScalarLength is equal to (u2ModLength) or (u2ModLength + 4)
For the ECDSA signature generation be sure to follow the directives given for the RNG on the chip you use (particularly initialization, seeding) and compulsorily start the RNG.
The scalar number k must be selected at random. This random must be generated before the call of the ECDSA signature. For this random generation be sure to follow the directives given for the RNG on the chip you use (particularly initialization, seeding) and compulsorily start the RNG.
The operation performed is:
- Compute the ECDSA (R,S) as described in FIPS 186-2, but leaving the user the role of computing the input Hash Value, thus leaving the freedom of using any other algorithm than SHA-1.
- Compute a R value using the input A point and the scalar number.
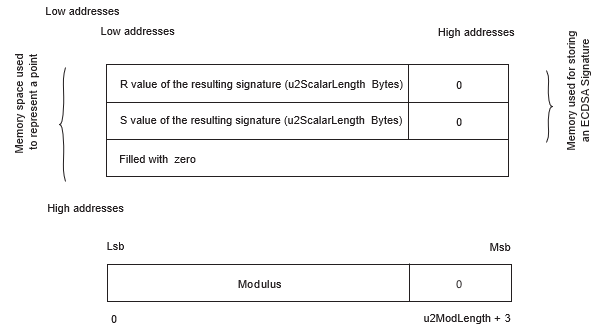
- Compute a S value using R, the scalar number, the private key and the provided hash value. Note that the resulting signature (R,S) is stored at the place of the input A point.
- If all is correct and S is different from zero, the status is set to PUKCL_OK. If all is correct and S equals zero,the status is set to PUKCL_WRONG_SELECT_NUMBER. If an error occurs, the status is set to the corresponding error value (see Status Returned Values below).
The service name for this operation is
ZpEcDsaGenerateFast.
This service uses Fast mode and Fast Modular
Reduction for computation.
- The signature (R,S), when resulting from a
computation is given back at address of
the A point:
- R output is at offset 0 and has length (u2ScalarLength + 4)bytes.
- S output is at offset (u2ScalarLength + 4) bytes and has length (u2ScalarLength + 4) bytes.
- The MSB 4 zero bytes may be suppressed to get the R and S values on u2ScalarLength bytes
Parameters Definition
| Parameter | Type | Direction | Location | Data Length | Before Executing the Service | After Executing the Service |
|---|---|---|---|---|---|---|
| nu1ModBase | nu1 | I | Crypto RAM | u2ModLength + 4 | Base of modulus P | Base of modulus P |
| nu1CnsBase | nu1 | I | Crypto RAM | u2ScalarLength + 8 | Base of Cns | Base of Cns |
| u2ModLength | u2 | I | – | – | Length of modulus P | Length of modulus P |
| nu1ScalarNumber | nu1 | I | Crypto RAM | u2ScalarLength + 4 | Scalar Number used to multiply the point A | Unchanged |
| nu1OrderPointBase | nu1 | I | Crypto RAM | u2ScalarLength + 4 | Order of the Point A in the elliptic curve | Unchanged |
| nu1PrivateKey | nu1 | I/O | Crypto RAM | u2ScalarLength + 4 | Base of the Private Key | Unchanged |
| nu1HashBase (see Note 1) | nu1 | I |
Crypto RAM |
u2ScalarLength + 4 | Base of the hash value resulting from the previous SHA |
Unchanged |
| u2ScalarLength | u2 | I | – | – | Length of scalar (same length as the length of order) | Length of scalar |
| nu1PointABase (see Note 2) | nu1 | I/O | Crypto RAM | 3*u2ModLength + 12 | Input point A (three coordinates (X,Y) affine and Z = 1) | Resulting signature (R,S,0) |
| nu1ABase | nu1 | I | Crypto RAM | u2ModLength + 4 | Parameter a of the elliptic curve | Unchanged |
| nu1Workspace | nu1 | I | Crypto RAM | 8*u2ModLength + 44 | – | Corrupted workspace |
- The hash value calculus is defined by the ECDSA norm and depends on the elliptic curve domain parameters. To construct the input parameter, the 4 Most Significant Bytes must be set to zero.
- The resulting signature format is different from the point A format (see Description above for information on the point A format).
Code Example
PUKCL_PARAM PUKCLParam;
PPUKCL_PARAM pvPUKCLParam = &PUKCLParam;
// ! The Random Number Generator must be initialized and started
// ! following the directives given for the RNG on the chip
PUKCL (u2Option) = 0;
// Depending on the option specified, not all fields should be filled PUKCL _ZpEcDsaGenerate(nu1ModBase) = <Base of the ram location of P>; PUKCL _ZpEcDsaGenerate(u2ModLength) = <Byte length of P>;
PUKCL _ZpEcDsaGenerate(nu1CnsBase) = <Base of the ram location of Cns>;
PUKCL _ZpEcDsaGenerate(nu1PointABase) = <Base of the A point>;
PUKCL _ZpEcDsaGenerate(nu1PrivateKey) = <Base of the Private Key>;
PUKCL _ZpEcDsaGenerate(nu1ScalarNumber) = <Base of the ScalarNumber>;
PUKCL _ZpEcDsaGenerate(nu1OrderPointBase) = <Base of the order of A point>;
PUKCL _ZpEcDsaGenerate(nu1ABase) = <Base of the a parameter of the curve>;
PUKCL _ZpEcDsaGenerate(nu1Workspace) = <Base of the workspace>;
PUKCL _ZpEcDsaGenerate(nu1HashBase) = <Base of the SHA resulting hash>;
PUKCL_ZpEcDsaGenerate(u2ScalarLength) = < Length of ScalarNumber>;
...
// vPUKCL_Process() is a macro command, which populates the service name
// and then calls the library...
vPUKCL_Process(ZpEcDsaGenerateFast, pvPUKCLParam);
if (PUKCL (u2Status) == PUKCL_OK)
{
...
}
else // Manage the error
Constraints
No overlapping between either input and output are allowed. The following conditions must be avoided to ensure that the service works correctly:
- nu1ModBase, nu1CnsBase, nu1PointABase, nu1PrivateKey, nu1ScalarNumber, nu1OrderPointBase,nu1ABase, nu1Workspace or nu1HashBase are not aligned on 32-bit boundaries
- {nu1ModBase, u2ModLength + 4}, {nu1CnsBase, u2ModLength + 8}, {nu1PointABase, 3*u2ModLength+ 12},{nu1PrivateKey, u2ScalarLength + 4},{nu1ScalarNumber, u2ScalarLength + 4},{nu1OrderPointBase, u2ScalarLength + 4}, {nu1ABase, u2ModLength + 4}, {nu1Workspace, <WorkspaceLength>} or {nu1HashBase, u2ScalarLength + 4} are not in Crypto RAM
- u2ModLength is either: < 12, > 0xffc or not a 32-bit length
- All overlapping between {nu1ModBase, u2ModLength + 4}, {nu1CnsBase, u2ModLength +8}, {nu1PointABase, 3*u2ModLength + 12}, {nu1PrivateKey, u2ScalarLength + 4}, {nu1ScalarNumber, u2ScalarLength + 4}, {nu1OrderPointBase, u2ScalarLength + 4}, {nu1ABase, u2ModLength + 4}, {nu1Workspace, <WorkspaceLength>} and {nu1HashBase, u2ScalarLength + 4}
Status Returned Values
| Returned Status | Importance | Meaning |
|---|---|---|
| PUKCL_OK | – | The computation passed without problem. The signature is the good one. |
| PUKCL_WRONG_SELECTNUMBER | Warning | The given value for nu1ScalarNumber is not good to perform this signature generation. |
