4.10.1.3 Security-Switch-Authentication Method Configuration
This section describes the security switch authentication method configuration, as shown in the following figure.
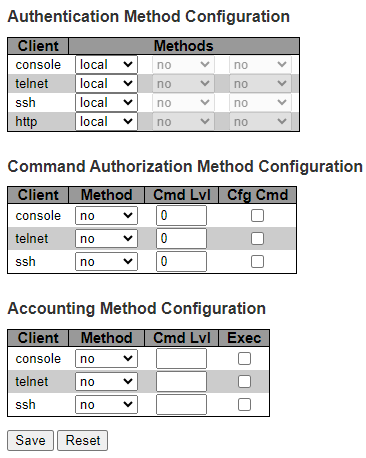
The list of parameters is as follows:
- Authentication Method Configuration: The authentication section allows you to configure how you are authenticated when you log into the switch through one of the management clients’ interfaces. The table has one row for each client type and several columns, which are:
- Client: The management client for which the configuration is applied.
- Methods: Method can be set to one of the following values:
- No: Authentication is disabled and login is not possible.
- Local: Use the local user database on the switch for authentication
- Radius: Use remote RADIUS server(s) for authentication
- TACACS: Use remote TACACS+ server(s) for authentication.
Methods that involve remote servers are timed out if the remote servers are offline. In this case, the next method is tried. Each method is tried from left to right and continues until a method either approves or rejects a user. If a remote server is used for primary authentication, it is recommended to configure secondary authentication as 'local'. This enables the management client to login using the local user database if none of the configured authentication servers are alive
- Command Authorization Method Configuration: The command authorization section allows you to limit the CLI commands available to a user. The table has one row for each client type and several columns, which are:
- Client: The management client for which the configuration is applied
- Method: Method can be set to one of the following values:
- No: Command authorization is disabled. User is granted access to CLI commands according to his privilege level
- TACACS: Use remote TACACS+ server(s) for command authorization. If all remote servers are offline, the user is granted access to CLI commands according to his privilege level.
- Cmd Lvl: Authorize all commands with a privilege level higher than or equal to this level. Valid values are in the range 0 to 15.
- Cfg Cmd: Also authorize configuration commands
- Accounting Method Configuration: The accounting section allows you to configure command and exec (login) accounting. The table has one row for each client type and several columns, which are:
- Client: The management client for which the configuration is applied
- Method: Method can be set to one of the following values:
- No: Accounting is disabled
- TACACS: Use remote TACACS+ server (s) for accounting
- Cmd Lvl: Enable accounting of all commands with a privilege level higher than or equal to this level. Valid values are in the range 0 to 15. Leave the field empty to disable command accounting.
- Exec: Enable exec (login) accounting
