4.8 DHCPv6 Snooping Configuration
Configure DHCPv6 (that is, DHCP over IPv6) Snooping on the Configuration > DHCPv6 > Snooping page. The following figure shows the DHCPv6 Snooping configuration table.
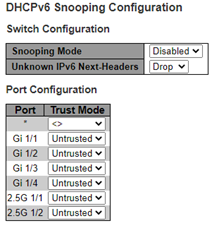
The list of the parameters is as follows:
- Snooping Mode: Indicates the DHCPv6 snooping mode operation. The following are the possible modes:
- Enabled: Enable DHCPv6 snooping mode operation. When DHCPv6 snooping mode operation is enabled, the DHCPv6 client request messages are forwarded to trusted ports and only allow reply packets from trusted ports.
- Disabled: Disable DHCP snooping mode operation
- Unknown IPv6 Next-Headers: Indicates how Unknown IPv6 Next-Header values must be treated. The switch must parse all IPv6 packets to a DHCPv6 client to determine if it is a DHCPv6 message. If an unknown IPv6 extension header is encountered, then the parsing cannot continue. See RFC 7610, section 5, item 3 for details. The following are the possible options:
- Drop: Drop packets with unknown IPv6 extension headers. This is the most secure option but may result in traffic disruptions.
- Allow: Allow packets with unknown IPv6 extension headers. This is a less secure option but prevents traffic disruptions.
- Port Mode Configuration: Indicates the DHCPv6 snooping port mode. Possible port modes are:
- Trusted: Configures the port as trusted source of the DHCPv6 messages
- Untrusted: Configures the port as untrusted source of the DHCPv6 messages
Note: Enabling this function requires changing the Key Type to MAC
and IP Address for all ports that receive DHCPv6 packets. You can do this on the
QoS Port Classification page.
