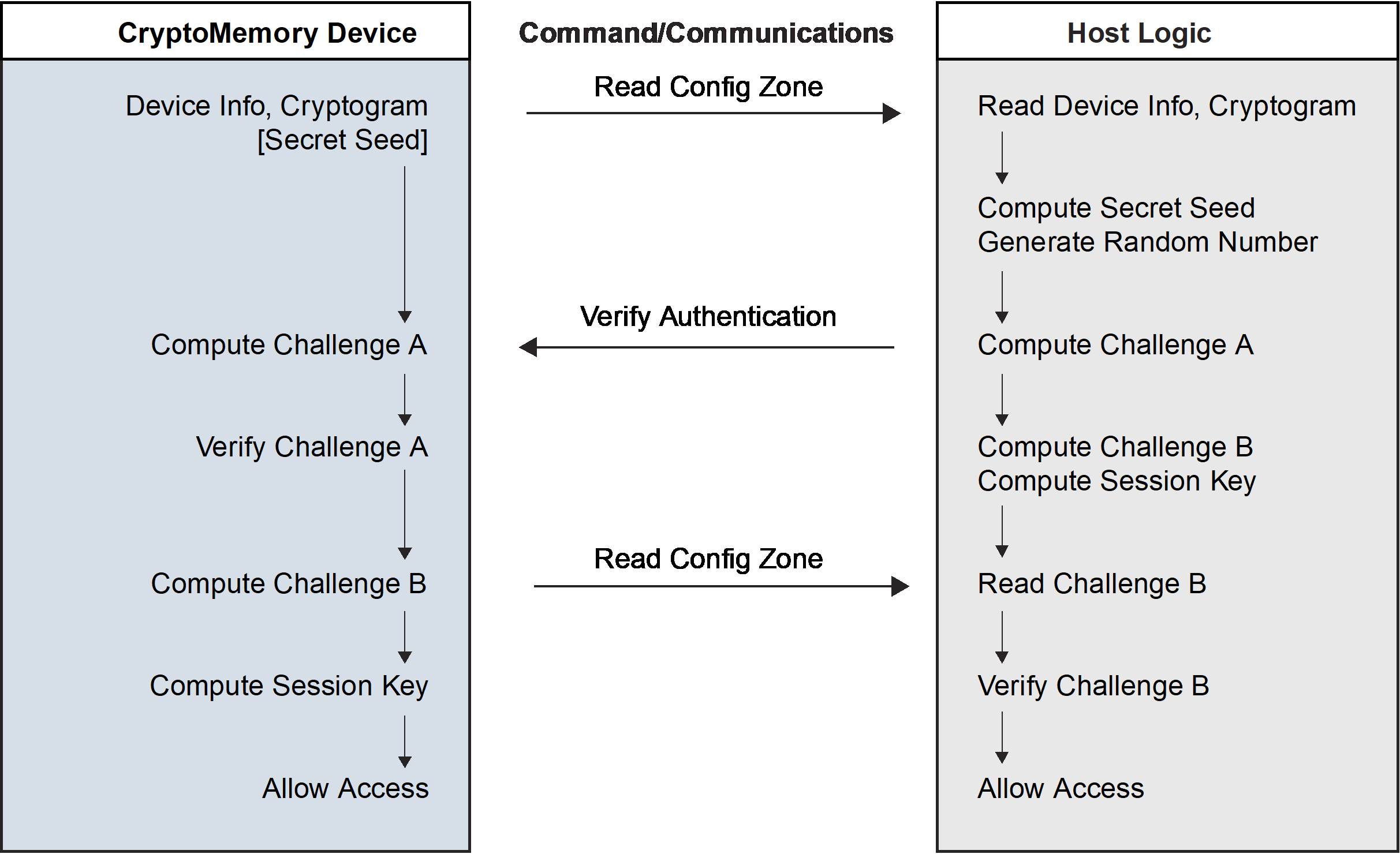
6.1.2 Authentication Protocol
The use of a mutual authentication protocol further protects access to user zones. Any one of four key sets is available for assignment to any user zone through configuration of access registers. Each key set consists of a secret seed, a cryptogram and a session encryption key. A Verify Crypto command exists to allow the use of any one of the key sets to enter Authentication mode. Each successful entry into Authentication mode renders the mode active for the current key set until the next call to the Verify Crypto command or device reset. Only one key set may be active at any time. Unsuccessful calls of the Verify Crypto command will exit Authentication mode and will decrement the value of the Authentication Attempts Counter (AAC) register. Decrementing the AAC to $00 permanently disables the corresponding key set and permanently renders the corresponding user zone(s) under protection inaccessible.
Entry into Authentication mode is a process through which the host and CryptoMemory® device mutually authenticate one another. First, the host generates a 64-bit random number, reads the current cryptogram and identification information from the device, and uses this information in conjunction with the corresponding secret seed to generate a 64-bit challenge for the device. The host also generates a new cryptogram and session encryption key in the process. The host then sends the challenge and random number to the device by calling the Verify Crypto command. The device utilizes the random number from the host to generate its own challenge, new cryptogram, and session encryption key. It then compares the challenge to the one from the host. If the challenges match, then the device declares the host authentic and overwrites its corresponding current cryptogram and session encryption key with the new ones. To complete the mutual authentication, the host reads the new cryptogram from the device and compares it with its own cryptogram. The new cryptogram from the device serves as a challenge to the host. If the cryptograms match, then the device is authentic. Only an authentic pair of host and device can generate the same challenges and cryptograms. Activating mutual authentication requires the use of the verify authentication variant of the Verify Crypto command (see section 8.2 Command Set and section 10.3 Command Set).