14.6.1.4.2 Cipher Block Chaining (CBC)
In CBC mode, the result of a previous AES operation is XORed with the new incoming vector forming the new plaintext to encrypt, see the figure below. This mode is used for the computation of a cryptographic checksum (message integrity code, MIC).
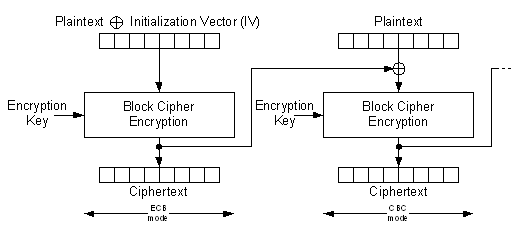
After preparing the AES key and defining the AES operation direction using AT86RF212B SRAM register bit AES_DIR, the data has to be provided to the AES engine and the CBC operation can be started.
The first CBC run has to be configured as ECB to process the initial data (plaintext XORed with an initialization vector provided by the microcontroller). All succeeding AES runs are to be configured as CBC by setting the AES_MODE bits in the AES_CTRL register to '2' (AES_CTRL.AES_MODE=2). The AES_DIR bit in the AES_CTRL register (AES_CTRL.AES_DIR) must be set to '0' to enable AES encryption. The data to be processed has to be transferred to the SRAM starting with address 0x84 to 0x93 (AES_STATE registers). Setting the AES_REQUEST bit in the AES_CTRL_MIRROR register to '1' (AES_CTRL_MIRROR.AES_REQUEST=1) starts the first encryption within one SRAM access. This causes the next 128 bits of plaintext data to be XORed with the previous cipher text data.
According to IEEE 802.15.4 the input for the very first CBC operation has to be prepared by a XORing a plaintext with an initialization vector (IV). The value of the initialization vector is zero. However, for non-compliant usage any other initialization vector can be used. This operation has to be prepared by the microcontroller.
