14.6.1.4.1 Electronic Code Book (ECB)
ECB is the basic operating mode of the security module. After setting up the initial AES key, AES_CTRL.AES_MODE = 0 sets up ECB mode. The AES_DIR bits in the AES_CTRL register (AES_CTRL.AES_DIR) selects the direction, either encryption or decryption. The data to be processed has to be written to SRAM addresses 0x84 through 0x93 (AES_STATE registers).
An example for a programming sequence is shown in the figure below. This example assumes a suitable key has been loaded before.
A security operation can be started within one SRAM access by appending the start command AES_REQUEST = 1 (register 0x94, AES_CTRL_MIRROR) to the SPI sequence. Register AES_CTRL_MIRROR is a mirrored version of register 0x83 (AES_CTRL).
Summarizing, the following steps are required to perform a security operation using only one AT86RF212B SPI access:
- Configure SPI access
- SRAM write
- Start address 0x83
- Configure AES operation
- address 0x83: select ECB mode, direction
- Write 128-bit data block
- addresses 0x84 – 0x93: either plain or ciphertext
- Start AES operation
- address 0x94: start AES operation, ECB mode
This sequence is recommended because the security operation is configured and started within one SPI transaction.
The ECB encryption and decryption operation is illustrated in the figures below.
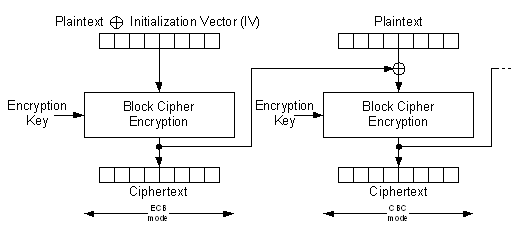
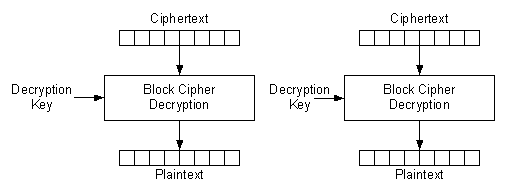
When decrypting, due to the nature of AES algorithm, the initial key to be used is not the same as the one used for encryption, but rather the last round key instead. This last round key is the content of the key address space stored after running one full encryption cycle, and must be saved for decryption. If the decryption key has not been saved, it has to be recomputed by first running a dummy encryption (of an arbitrary plaintext) using the original encryption key, then fetching the resulting round key from the key memory, and writing it back into the key memory as the decryption key.
ECB decryption is not used by either IEEE 802.15.4 or ZigBee frame security. Both of these standards do not directly encrypt the payload, but rather a nonce instead, and protect the payload by applying an XOR operation between the resulting (AES-) cipher text and the original payload. As the nonce is the same for encryption and decryption only ECB encryption is required. Decryption is performed by XORing the received cipher text with its own encryption result respectively, which results in the original plaintext payload upon success.
