4.10.2.1.1 Port Security Configuration
The Port Security Configuration page allows you to configure the Port Security global and per-port settings. Port Security allows for limiting the number of users on a given port. A user is identified by a MAC address and VLAN ID. If Port Security is enabled on a port, the limit specifies the maximum number of users on the port. If this number is exceeded, then an action is taken depending on the violation mode. The violation mode can be one of the following options. The Port Security configuration consists of two sections, a global and a per-port, as shown in the following figure.
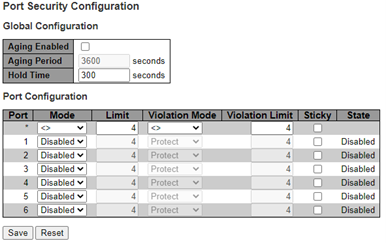
The Port Security Configuration page has the following parameters:
- Global Configuration
- Aging Enabled: If checked, the secured MAC addresses are subject to aging, as discussed under Aging Period.
- Aging Period: If Aging Enabled is checked, then the aging period is controlled with this input. If other modules are using the underlying functionality for securing MAC addresses, then they may have other requirements for the aging period. The underlying functionality uses the shorter requested aging period of all modules that have aging enabled. The Aging Period can be set to a number between 10s–10000000s with a default of 3600s. To understand why aging may be desired, consider the following scenario: An end-host is connected to a third-party switch or hub, which in turn is connected to a port on this switch on which Port Security is enabled. The end-host is allowed to forward if the limit is not exceeded. Consider that the end-host logs off or powers down. If there is no aging, then the end-host continues to take up resources on this switch and is allowed to forward. To overcome this situation, enable aging. With aging enabled, a timer is started once the end-host gets secured. When the timer expires, the switch starts looking for frames from the end-host, and if such frames are not seen within the next Aging Period, then the end-host is disconnected, and the corresponding resources are freed on the switch.
- Hold Time: It is measured in seconds. The Hold Time is used to determine how long a MAC address is held in the MAC table if it has violated the limit. The valid range is between 10s–10000000s with a default of 300s. The reason for holding a violating MAC address in the MAC table is primarily to ensure that the same MAC address does not give rise to continuous notifications (if notifications on violation count is enabled).
- Port Configuration: The table has one row for each port on the switch and several columns, which are as follows:
- Port: The port number to which the configuration below applies
- Mode: Controls whether
Port Security is enabled on this port.Note: Other modules may still use the underlying port security features without enabling Port Security on a given port.
- Limit: The maximum number of MAC addresses that can be secured on this port. This number cannot exceed 1023. Default is 4. If the limit is exceeded, then an action is taken corresponding to the mode. The switch is born with a total number of MAC addresses from which all ports draw whenever a new MAC address is seen on a Port Security-enabled port. As all ports draw from the same pool, a configured maximum might not be granted if the remaining ports have already used all available MAC addresses.
- Violation Mode: If Limit
is reached, then the switch can take one of the following actions:
- Protect: Do not allow more than Limit MAC addresses on the port but take no further action
- Restrict: If Limit is reached, then the subsequent MAC addresses on the port are counted and marked as violating. Such MAC addresses are removed from the MAC table when the hold time expires. At the most, Violation Limit MAC addresses can be marked as violating at any given time.
- Shutdown: If Limit is reached, then one
additional MAC address causes the port to be shut down. This implies
that all secured MAC addresses be removed from the port, and no new
addresses be learned. There are three ways to re-open the port:
- In the Configuration > Ports page's Configured column, disable the port and then restore the original mode
- Make a Port Security configuration change on the port
- Boot the switch
- Violation Limit: The maximum number of MAC addresses that can be marked as violating on this port. This number cannot exceed 1023. Default is 4. It is only used when Violation mode is Restrict.
- Sticky: Enables sticky learning of MAC
addresses on this port. When the port is in sticky mode, all MAC addresses that
would otherwise have been learned as dynamic are learned as sticky. Sticky MAC
addresses are part of the
running-configand can therefore be saved tostartup-config. Sticky MAC addresses survive link changes (in contrast to Dynamic, which has to be learned again). They also survive reboots if running-config is saved to startup-config. A port can be Sticky-enabled whether Port Security is enabled on that interface or not. In that way, it is possible to add sticky MAC addresses management wise before enabling Port Security. To do this, go to Configuration > Security > Port Security > MAC Addresses page. - State: This column shows the current Port Security state of the port. The state takes one of four values:
- Disabled: Port Security is disabled on the port
- Ready: The limit is not yet reached. This can be shown for all violation modes.
- Limit Reached: Indicates that the limit is reached on this port. This can be shown for all violation modes.
- Shutdown: Indicates that the port is shut down by Port Security. This state can only be shown if violation mode is set to shut down.
